DNS Security: How DNS Works and How CoreTech Protects It

The Domain Name System (DNS) serves as a cornerstone of the internet, quietly operating behind the scenes to link website names entered into search boxes with their corresponding IP addresses—a string of numbers far beyond human memory capabilities. DNS security is critical to ensure the smooth functioning of this system, protecting it from a wide range of DNS attacks.
What is DNS?
Though typing an IP address directly into a browser remains an option, the preference for user-friendly domain names is evident. DNS stepped in to replace an unsustainable manual matching process, which in the early days tasked one individual—Elizabeth Feinler at Stanford Research Institute—with maintaining a master list of all internet-connected computers. In 1983, Paul Mockapetris introduced DNS, a scalable and automated system facilitating domain-name-to-IP-address translation.
DNS has a distributed design, allowing multiple servers to distribute the workload. With over 342 million registered domains, a centralized directory would prove impractical. Instead, domain name servers globally share information, ensuring updates and eliminating redundancies.
Performance optimization is another key aspect of DNS’s design. Distributing requests among numerous servers prevents bottlenecks. Consider the scenario where worldwide requests to resolve the domain name “Google” were funneled to a single location—DNS information sharing among multiple servers mitigates this issue. Consequently, a single domain may have multiple IP addresses, directing users to different servers based on their geographic location.
How does DNS operate?
When a computer seeks the IP address associated with a domain name, it initiates a DNS query through a DNS client. This query cascades through recursive resolvers, ultimately reaching authoritative name servers that hold the information to fulfill the request.
DNS operates through a hierarchical structure. Initially, a query is made to a recursive resolver, which then leads to a root server. Root servers are located globally, so the system routes the request to the closest one. The query is then passed to a top-level domain (TLD) nameserver, responsible for the second-level domain (the words typed into the search box). Finally, the query reaches the domain nameserver, which looks up the IP address and sends it back to the client device—completing the process in milliseconds.
DNS numbering system
Any device connected to the Internet needs to have a unique IP address in order to have traffic properly routed to it. The DNS numbering system translates human queries into numeric values using IPv4 or IPv6. IPv4 utilizes 32-bit integers expressed in decimal notation, while IPv6 employs 128-bit-sized numbers, significantly expanding the address space. The string of numbers is divided into multiple sections – the network component, the host, and the subnet. The network part designates the class and category of the network that is assigned to that number. The host identifies the specific machine on the network. The subnet part of the number is optional but is used to navigate the extremely large number of subnets and other partitions within a local network.
Identifying your DNS server
Typically, your DNS server is established by your Internet Service Provider (ISP). However, users can opt for public DNS servers like Google’s (8.8.8.8) for recursive resolution. Many other public DNS options are available as well.
DNS and security and cyber threats
DNS and DDoS security
DNS servers are prime targets for DDoS attacks due to their critical role in translating website names into IP addresses and the massive impact it can have on one’s business. To give an example, one of the most popular DDoS attacks directed against a major DNS provider took place in October 2016, when a large and well-distributed DDoS attack targeted Dyn, one of the main global DNS providers. This attack caused widespread outages for many popular websites, including Twitter, Reddit, and Spotify, by overwhelming their servers with a massive flood of traffic. This attack highlighted the vulnerability of DNS providers and the cascading effects such attacks can have on a big portion of the Internet. (https://en.wikipedia.org/wiki/DDoS_attacks_on_Dyn).
Here are some of the most popular DDoS attacks used against DNS:
Volumetric Attacks: these overwhelm the DNS server with a massive flood of traffic, like a giant data wave. This makes the server overloaded and unable to respond to legitimate requests.
DNS Amplification Attacks: these exploit vulnerabilities in third-party servers to amplify the attack traffic. Attackers send small requests to vulnerable servers configured to respond with much larger replies, directing those responses toward the DNS server. This magnifies the attack’s impact significantly.
UDP Floods: these bombard the DNS server with User Datagram Protocol (UDP) packets, a connectionless protocol that doesn’t require confirmation from the receiving end. This consumes server resources and disrupts its ability to handle legitimate queries.
Cache Poisoning Attacks: these aim to manipulate the DNS cache by injecting false information. If successful, users trying to access a website might be redirected to a malicious one instead.
These are just some of the common methods, and attackers are constantly developing new techniques.
How CoreTech protects DNS efficiently
At CoreTech, we’ve developed a bespoke, multi-layered DDoS security solution tailored specifically for DNS servers. Our comprehensive approach includes:
1. Volumetric DDoS Automatic Filtering – utilizing standard ACL rules at the network edge, we implement intelligent rate-limiting for the most common DDoS vectors, effectively mitigating approximately 85-90% of the attack volume. Additionally, our proprietary adaptive filtering technology targets UDP-based attacks, automatically blocking them with high efficiency while not generating false positives. This is particularly crucial for securing UDP-based applications like DNS server traffic.
2. Global Stateful Firewall – our cloud stateful firewall deployed over all 20 PoPs, allows you to create a customized cybersecurity profile for each unique IP address within your network. For example, if your DNS server is hosted at IP address 1.2.3.4/32, our tool enables you to selectively permit UDP traffic specifically destined for port 53, while blocking any other unauthorized traffic. Any rule you create in the firewall is synchronized over the entire network and your traffic is always prefiltered accordingly, before reaching your network.
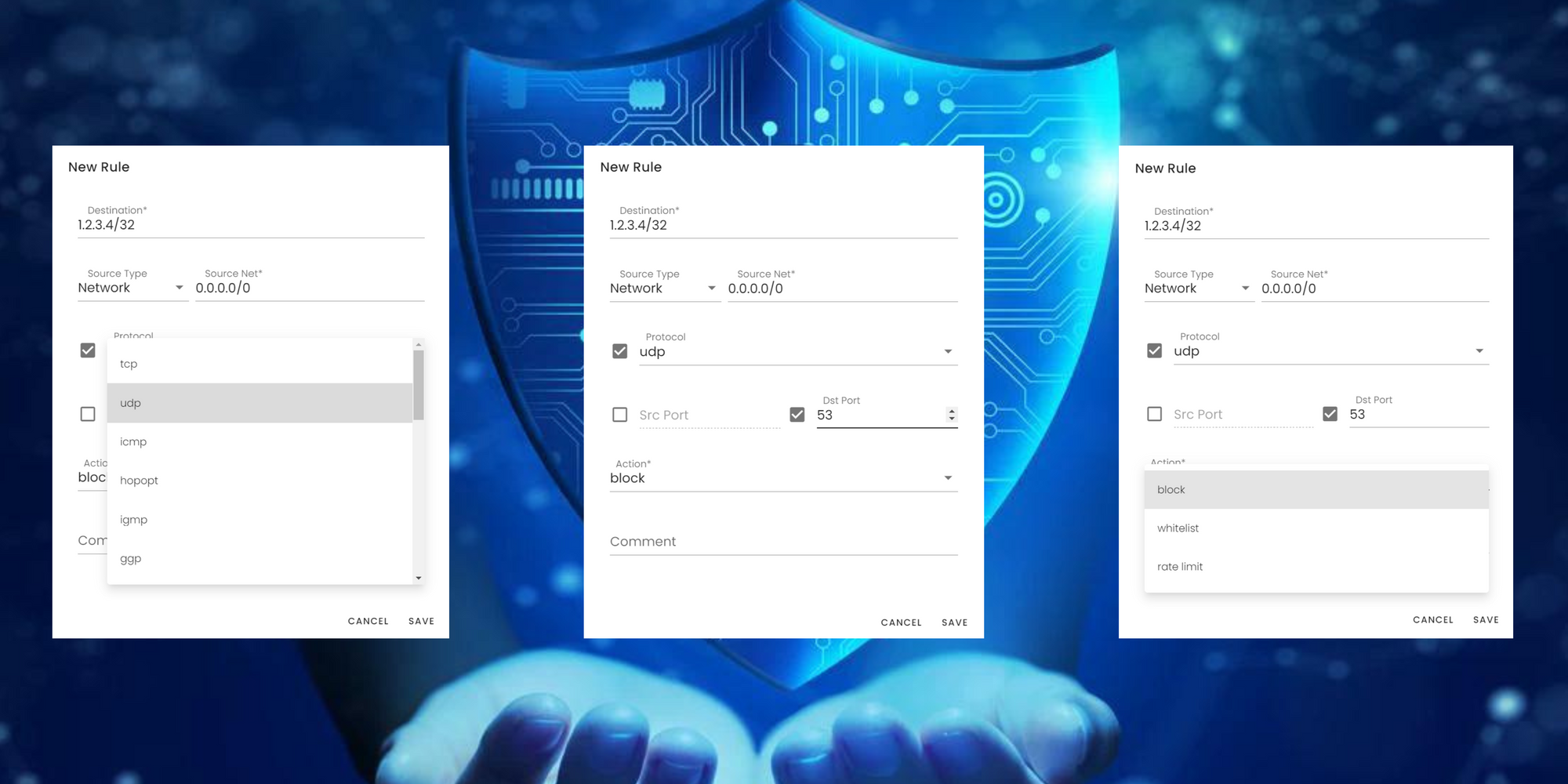
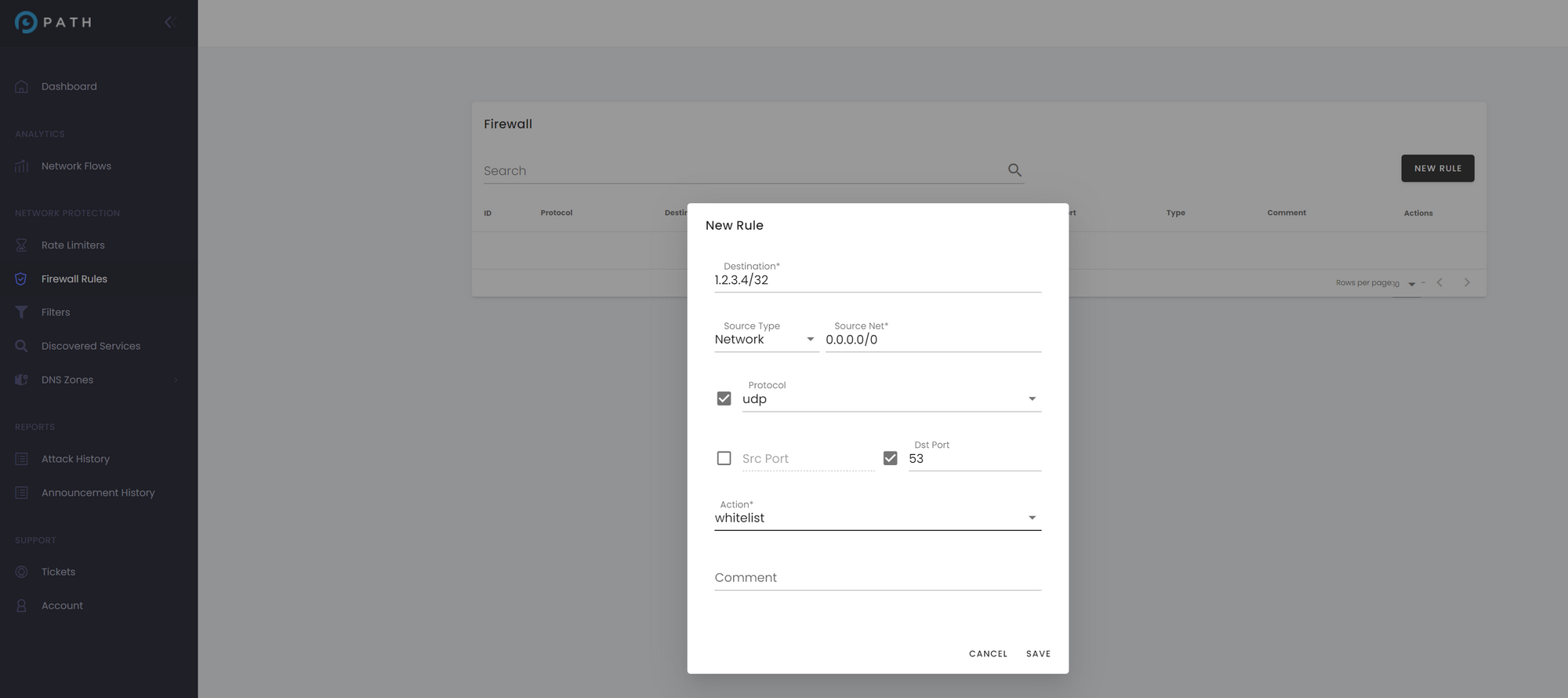
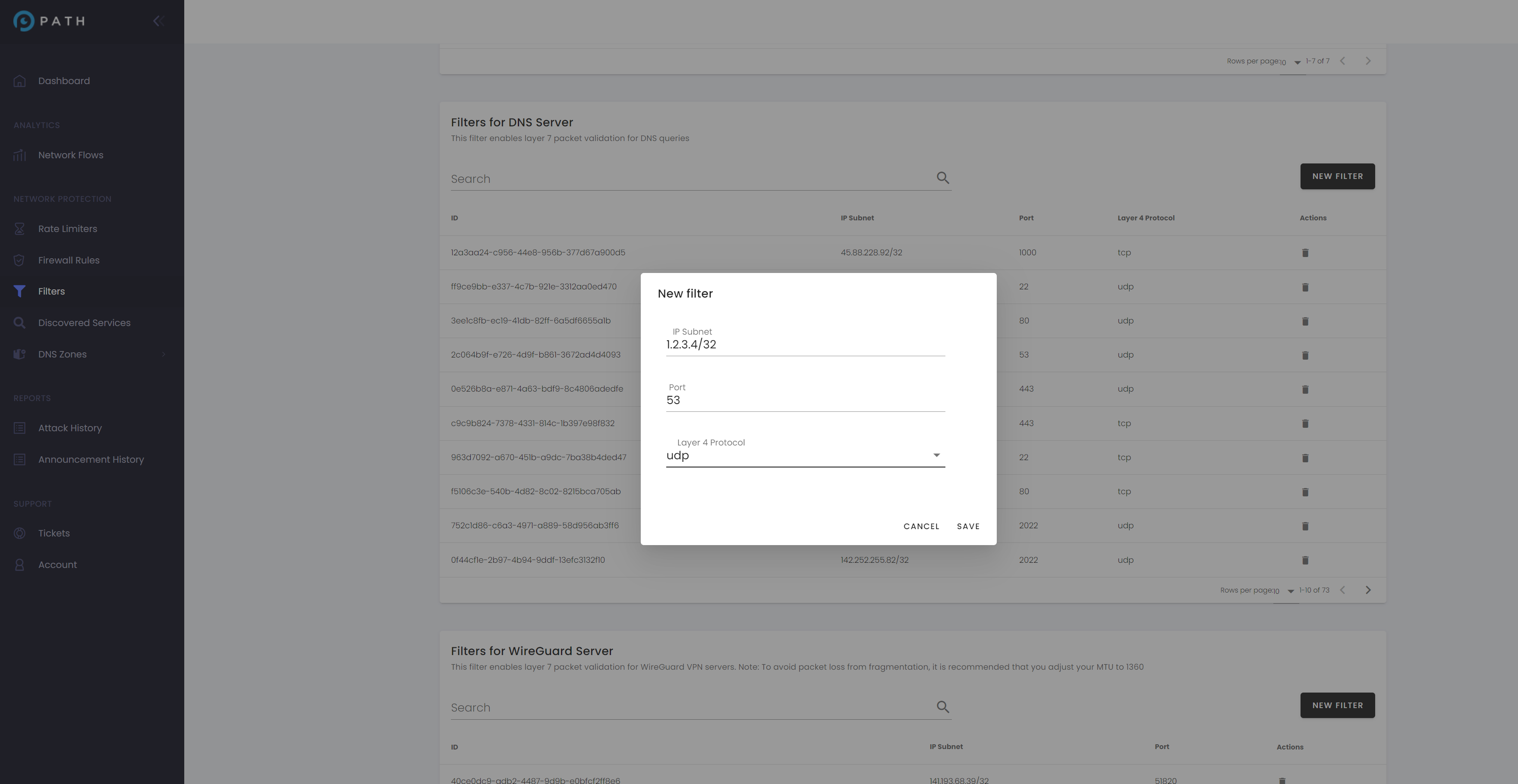
3. Custom-Built eXpress Data Path (XDP) DDoS Filter for DNS Server Traffic – The Domain Name System (DNS) protocol is registered in the RFC (Request for Comments) documents by the IETF – https://www.ietf.org/rfc/rfc1035.txt. Recognizing the critical importance of adhering to standardized DNS protocols, our team has engineered an XDP-based DDoS filter specifically tailored for DNS. This filter meticulously inspects incoming traffic, ensuring strict compliance with the DNS protocol as outlined in RFC documentation. Customers can easily configure and activate the DNS Server filter via our intuitive dashboard, specifying the IP address, port (e.g., 53), and UDP protocol they wish to protect.
By seamlessly integrating these three layers of defense, our DDoS mitigation solution is truly efficient in safeguarding your DNS server against malicious attacks. As a testament to our technological prowess, CoreTech proudly secures the infrastructure of numerous leading global DNS service providers.
Ready to fortify your DNS infrastructure against the ever-evolving DDoS threat? Contact us now at info@coretechnologys.com to schedule a consultation and take the first step towards enhancing your cybersecurity posture.

